When Source Code Hides in Plain Sight – Introducing SVN-Ripper
Imagine this: A company has a well-designed web application, hosted securely and hardened externally, and yet the entire source code is retrievable by simply browsing to:
https://yourdomain.com/.svn/
This situation is not hypothetical. During multiple red team and pentest engagements at Pretera, we discovered complete application logic exposed through Subversion (SVN) metadata folders that were inadvertently deployed to production. We found the same vulnerability occuring with .git repositories as well.
What’s the Risk?
These .svn folders are remnants from legacy version control systems. When left accessible in production environments, they allow attackers to:
- Rebuild the full directory structure of the site
- Access internal scripts, configuration files, and sensitive credentials
- Analyze business logic and discover hidden vulnerabilities
- Leak proprietary algorithms and client data
For industries such as finance, healthcare, e-commerce, or SaaS, the consequences can include:
- Regulatory non-compliance (e.g., GDPR, HIPAA)
- Credential stuffing or account takeover
- Reputational damage and brand loss
- Competitive intelligence theft
Introducing: SVN-Ripper
To address this problem quickly and at scale, we developed SVN-Ripper, an open-source Python tool that detects and recovers source code from publicly exposed .svn folders.
Whether you're a pentester, red teamer, bug bounty hunter, or blue team defender, SVN-Ripper provides you real, structured output, not just a list of filenames.
You can download SVN-Ripper on GitHub: https://github.com/Pretera/SVN-Ripper
Bonus Tool: find_svn.py
Finding .svn leaks manually across the web can be slow and tedious.
Enter find_svn.py, our reconnaissance companion script that helps you discover hundreds or thousands of .svn/ URLs using:
- Google Dorking
- Bing Search API
- SerpAPI (Google Search API)
You can generate a large list of .svn-exposed URLs with:
python3 find_svn.py --engine google --max 15 --delay 3
Or use SerpAPI or Bing:
python3 find_svn.py --engine serpapi --serpapi-key YOUR_API_KEY
Save the output to a file, then run svn_ripper.py on the whole list:
python3 svn_ripper.py -l exposed.txt
This allows mass validation and extraction across large scopes such as bug bounty, supply chain, or vendor ecosystems.
Key Features of SVN-Ripper
- Auto-download
.svn/entriesfiles - Reconstruct the original folder structure
- Decode and restore
*.svn-basefiles to readable format (e.g.,.php,.js,.pdf) - HTML and JSON reporting
- ZIP packaging of recovered files
- Proxy support for Burp Suite or WAF bypass
Example Usage
Basic usage:
python3 svn_ripper.py -u https://target.com/.svn/
Advanced batch processing:
python3 svn_ripper.py -l exposed.txt \
--output-dir leaks \
--json report.json \
--filter .php,.env,.conf \
--use-proxy http://127.0.0.1:8080
Business Use Cases
| Role | How SVN-Ripper Helps |
|---|---|
| Pentesters | Leverage metadata exposure to gain access or escalate findings |
| Bug Bounty | Recover scope logic from exposed SVN repos |
| Defenders | Confirm leaks, validate cleanup post-incident |
| CISOs | Communicate risk using tangible, decoded examples |
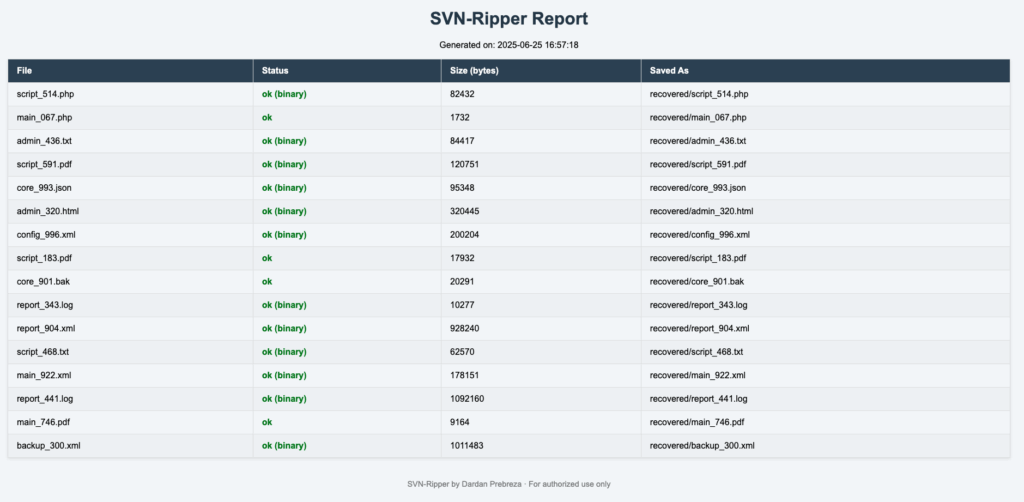
Demo Screenshot
Recommendations
If you're on a development, operations, or security team:
- Never deploy
.svn/to production environments - Block access to
.svnusing.htaccess, NGINX, or web firewalls - Regularly scan your internet-facing assets using SVN-Ripper and find_svn.py
- Integrate detection into CI/CD or external asset monitoring pipelines
Need Help?
Pretera specializes in identifying overlooked risks like this during:
- Application Penetration Tests
- Cloud & Infrastructure Audits
- M&A and Supply Chain Security Reviews
Contact Pretera to find the weaknesses before attackers do.