Posts by pretera
Azure as a Hiding Spot for Exfiltrated Data
Jaeger is a tool created for data exfiltration to Azure Blob Containers that will assist purple teams to analyze the infrastructure of an organization against data exfiltration. Jaeger is named after the arctic bird Parasitic Jaeger, which tends to steal food from other birds. This tool is built in Go programming language, and has many…
Read MoreBugcrowd and Pretera Join Forces to Accelerate Proactive Security for Enterprises
Brussels-based security specialist adds global reach and continuous testing to offensive security portfolio SAN FRANCISCO, CA & BRUSSELS, BELGIUM – 19 August 2025 – Bugcrowd, a crowdsourced security leader, today announced a strategic collaboration with Pretera, an offensive security firm based in Brussels. As Bugcrowd’s first partner in the Benelux region, Pretera will play a key role in…
Read MoreWeaponizing Cross-Site Scripting (XSS) Attacks – Exploitation Ideas and Maximizing Impact
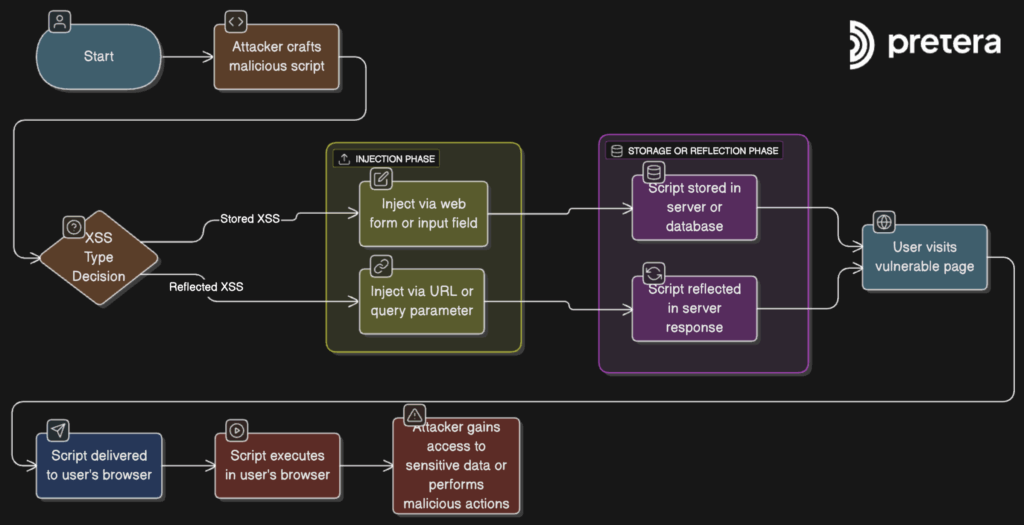
This blog post will explain that a simple alert() is not enough to demonstrate XSS impact. This blog will present ideas and suggestions about XSS exploitation, can include different methods of account takeovers, fake login pages, redirects, etc. Overview Cross-Site Scripting (XSS) ranks among the most frequently discovered vulnerabilities in web applications, yet it is…
Read MoreWhen Source Code Hides in Plain Sight – Introducing SVN-Ripper
Imagine this: A company has a well-designed web application, hosted securely and hardened externally, and yet the entire source code is retrievable by simply browsing to: https://yourdomain.com/.svn/ This situation is not hypothetical. During multiple red team and pentest engagements at Pretera, we discovered complete application logic exposed through Subversion (SVN) metadata folders that were inadvertently…
Read MoreDiving into ToolShell SharePoint RCE (CVE-2025–53770)
Meet CVE-2025–53770, a zero-click, unauthenticated remote code execution (RCE) bug in Microsoft SharePoint Server that’s currently being exploited in the wild. It’s dangerous and not a particularly complex exploit, which is why the internet is going bonkers about it. Timeline Overview Back in May 2025 l0gg, a security researcher at Pwn2Own Berlin, discovered a combo…
Read MorePretera Welcomes Former Swift CSO Karel De Kneef as External Strategic Advisor
Pretera, a cybersecurity firm specializing in offensive security and red teaming, is proud to announce that Karel De Kneef, former Chief Security Officer (CSO) of Swift, has joined the company as an External Strategic Advisor. Karel is a seasoned executive with more than two decades of leadership experience spanning technology, operations, and cybersecurity. During his…
Read MoreSliver Bullet – Staging & Shellcode Process Injection
In recent years, open-source adversary simulation tools have significantly matured. Sliver by Bishop Fox stands out among them, offering a free, open-source modern C2 framework with features once exclusive to commercial platforms. Here’s how our security consultant, Kinseb, got hands-on with it, from setup to first callback. Introduction This post is a technical walkthrough of…
Read MorePassword Reset Gone Wrong: The Power of Callback URL Manipulation
Account takeover by password reset is a common yet often overlooked flaw in which an attacker acquires access to a victim’s account by manipulating the password reset process. This type of flaw frequently targets flaws in how a website or service handles callback URLs, which are intended to redirect users after they reset their passwords.…
Read MoreDeepfake Attacks: The Latest Weapon of Social Engineering
Often overlooked, social engineering has always been a great weapon for cybercriminals due to its focus on exploiting human weaknesses. Social engineering takes a different approach compared to traditional hacking: instead of focusing on exploiting software vulnerabilities, it seeks to manipulate human weaknesses. It relies on manipulating emotions like trust, fear, and respect for authority,…
Read MoreBurp suite certified practitioner exam: Review and Insights
Since I recently passed the “Burp Suite Certified Practitioner” exam, I felt it would be useful to share some of my experiences and lessons learned, with those who are considering taking this exam, or just interested in completing the PortSwigger Academy challenges. How Did I Prepare Despite the fact that I have spent several years…
Read More